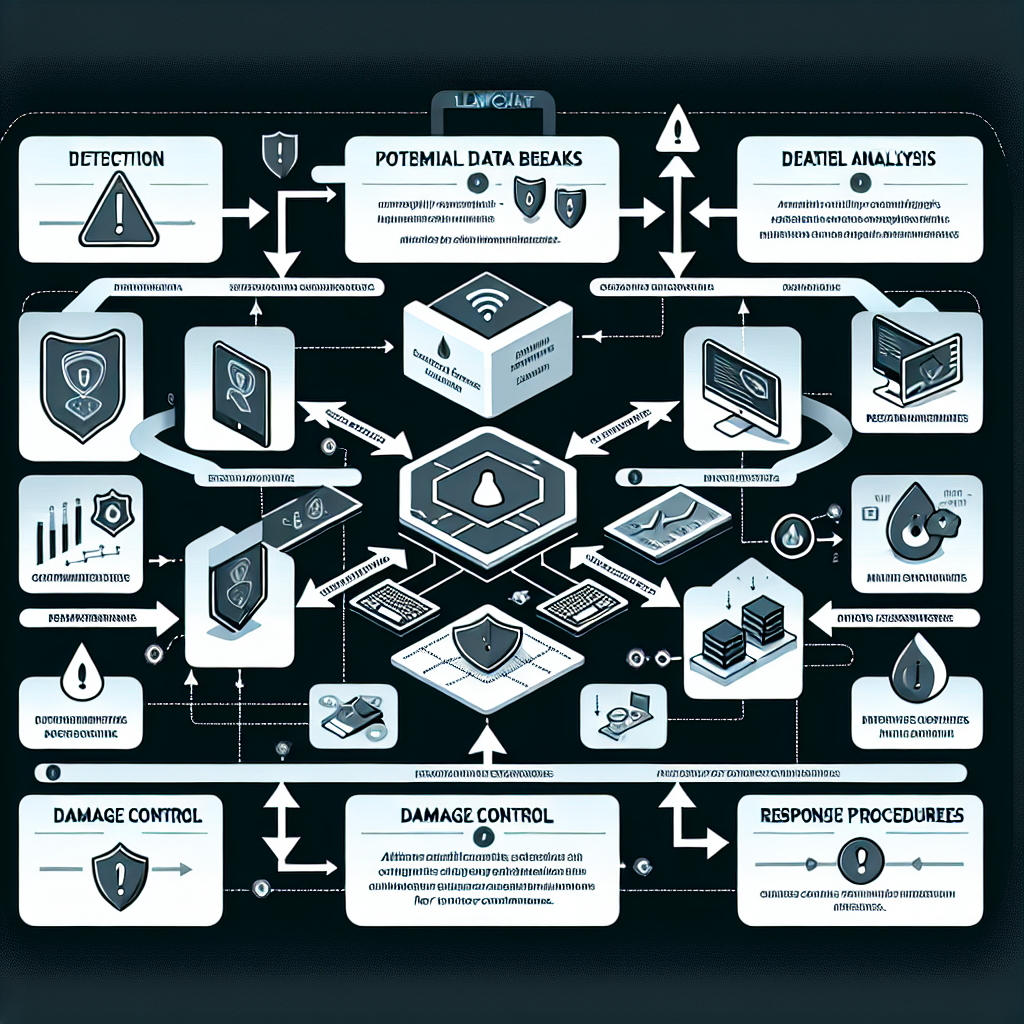
A flowchart that visually represents the process of monitoring data leaks on the dark web and rapidly responding to them. The chart begins with the detection of potential data breaches, flows into detailed analysis, proceeds towards determining the veracity of the threat, and finally outlines response procedures. Response procedures should include alerting relevant stakeholders, employing necessary countermeasures, and engaging in damage control and prevention measures for future occurrences. The style of the flowchart is professional and clear, with different stages represented by geometric shapes connected by directed arrows.
A flowchart that visually represents the process of monitoring data leaks on the dark web and rapidly responding to them. The chart begins with the detection of potential data breaches, flows into detailed analysis, proceeds towards determining the veracity of the threat, and finally outlines response procedures. Response procedures should include alerting relevant stakeholders, employing necessary countermeasures, and engaging in damage control and prevention measures for future occurrences. The style of the flowchart is professional and clear, with different stages represented by geometric shapes connected by directed arrows.
AI模型: DALL·E V3
出版日期: 4 个月前